The True Cost of a Business Cyber Breach
Sadly, there are plenty of bad agents acting against businesses to steal their data. Here's what could happen if you don't invest in better business resilience.
Unsure if your business has adequate layered security for your digital assets? Read on because today, we'll cover precisely what layered security looks like and how you can achieve it.
Welcome to another Westway IT guide!
In 2023, security breaches cost businesses an average of £1,100 per incident in the UK. According to a government survey, the cost increased to £4,960 for medium to larger enterprises. At the same time, cyber hygiene fell to 60-70%, leaving hackers with increasing opportunities to target businesses like yours.
Layered security is a comprehensive approach to safeguarding your business against digital threats. It works by implementing multiple overlapping security measures at different levels of your IT infrastructure.
The concept of multiple overlapping layers is deceptively simple yet extraordinarily effective. It's the idea that relying on a single solution, like an antivirus program, cannot protect your business alone. Just as a bank doesn't secure its vault with just one lock, your digital assets require a multifaceted approach to guard against cyber threats.
Typically, our approach to layered security is three-fold.
If you consider each element makes the side of a triangle, that will look something like this.
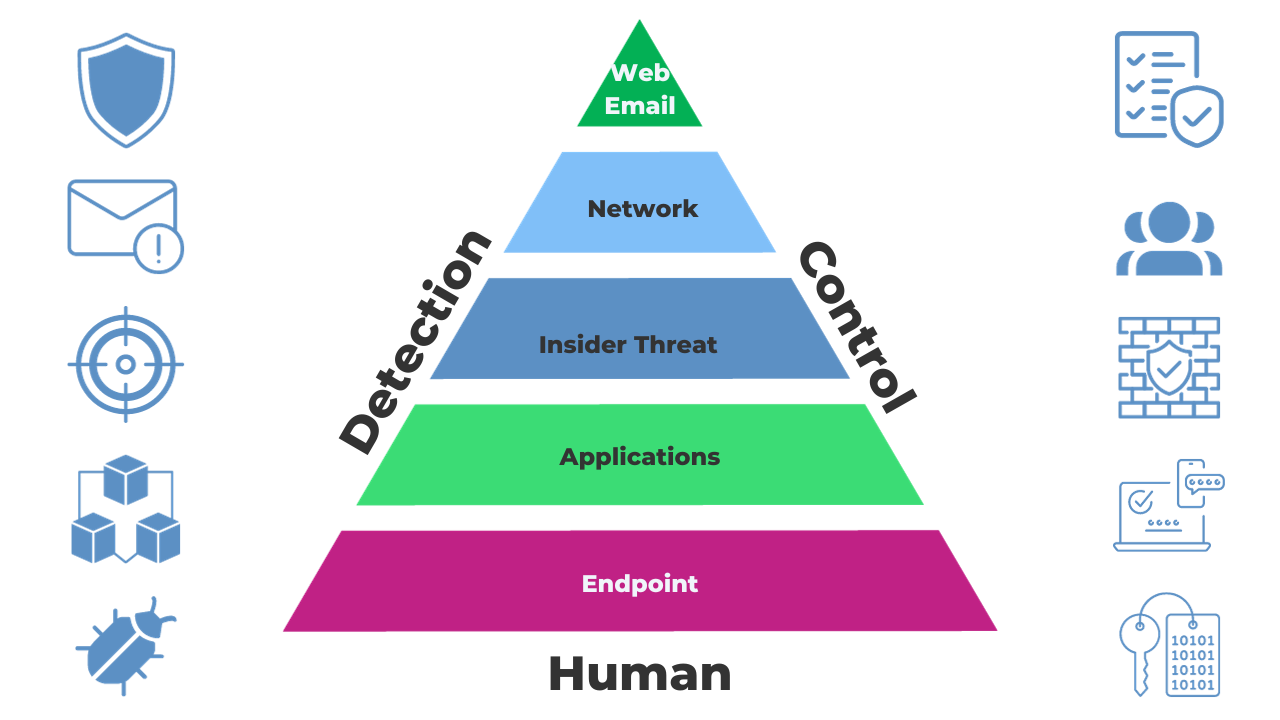
At the core of layered security lies your capability to detect when something suspicious happens within your digital environment. This is your early warning system. Think of it as the watchful eye that spots intruders at the gate.
Detection involves using tools and technologies to monitor network traffic, system logs, and user behaviours. The objective is identifying unusual or suspicious activities that could suggest a security breach.
Detection mechanisms include:
Effective detection ensures that you are aware of potential threats as soon as they arise, allowing for a swift and targeted response.
Controlling what abilities individuals and entities have within your system is critical. It involves limiting access, monitoring privileges, and enforcing data protection policies.
Control mechanisms include:
Control mechanisms are about setting rules, boundaries, and permissions to maintain the integrity of your digital assets.
Your employees play a pivotal role. They can identify irregular activities, report potential threats, and follow security protocols. Their vigilance and awareness can make or break your security.
Employees can:
Okay, so we have our triangle. Within these 3 elements are 5 overlapping layers.
This is the top layer and first line of defence, facing the vast expanse of the internet. Essential security measures at this level include:
Within your network, further security measures protect the information and resources you've built from outside attacks. These include:
This level is particularly significant because it addresses the risks that originate from within your organisation. Measures include:
To prevent vulnerabilities and breaches, your software and services must be fortified. Critical security measures here include:
Every device, from PCs to mobile phones, is a potential entry point for cyber threats. Securing these endpoints is paramount, and measures include:
Business resilience refers to your ability to withstand disruptions and adapt to change. Your IT security is intrinsically linked to business resilience for several reasons:
For some businesses, managing layered security in-house can be a complex task. Dedicated managed security service providers (MSSPs) offer a viable solution. They specialise in securing businesses and can tailor a layered security strategy to your needs.
If you are a smaller business, you will be looking for reliable managed IT services, just as we offer at Westway IT. Managed IT solutions cater for your security needs alongside other beneficial IT services, like hardware and software management and IT helpdesks.
Getting the right help can make all the difference as you maintain and grow your business, especially in securing your assets.
Need a chat about your layered security and business resilience? Book a 15-minute video call with John today!

John Fisher
Meet John Fisher, founder of Westway IT, passionate about helping businesses thrive with technology. With a BSc in Computer Science, he values integrity, education, and quality relationships. Active in The Tech Tribe and GTIA, John simplifies IT and creates scalable strategies. Connect with him on LinkedIn.