The True Cost of a Business Cyber Breach
Sadly, there are plenty of bad agents acting against businesses to steal their data. Here's what could happen if you don't invest in better business resilience.
Worried about cyberattacks against your business? As a trusted cybersecurity consultant to SMEs, I understand the gravity of your concern, so I put down my thoughts on the subject - because I believe total protection is unachievable.
There, I said it. But please don't panic. You can still be as close to total protection as possible if you take the proper measures, but I also want you to consider how to manage and mitigate breaches. You see, that's often overlooked and will be critical in navigating a world where cyberattacks are evolving daily.
Read on and let me explain.
In today's digitally driven world, the reality of cyber threats is undeniable. Whether you run a small bakery, a mid-sized law firm, or a large corporation, your business is constantly under the shadow of potential cyberattacks. Cybersecurity is not an issue exclusive to tech giants or banks; it's a universal concern that touches every sector and size of business.
Recent data from leading cybersecurity companies paints a concerning picture. The frequency and sophistication of cyberattacks are on a relentless rise. Hackers, who often operate with well-organised and well-funded teams, continuously scan the digital landscape for vulnerabilities. They are also tapping into the latest AI and machine learning to help them. This persistent effort highlights the stark reality that no business is immune to these threats.
I see it plainly with the SMEs I work with; we are under increasing pressure from more sophisticated attacks. That's why I recently rolled out my updated "cyber resiliency package" to all my clients - I'm preempting cyber threats with a more advanced approach to security management.
I often explain it like this: Your cybersecurity system is like fire protection. Fire alarms, extinguishers and sprinklers won't stop a fire from starting, but they minimise the impact and damage. As business owners, accepting the inevitability of cybersecurity incidents is crucial.
While perfection in cybersecurity may be elusive, preparedness is not. Business owners who are informed and proactive stand a better chance of protecting their assets. Remember, your goal isn't to eliminate all risks but to manage and mitigate them. By understanding the threat landscape and adopting a proactive mindset, you can significantly reduce the risks to your business.
In this context, business resilience becomes the key to survival. It's not about preventing every threat but about bouncing back swiftly and effectively when an incident occurs - understanding best practices that can help you bolster your business defences, reduce vulnerabilities, and enhance your organisation's ability to respond to incidents. There are many service options out there; if you need help deciding what’s right for you, drop me a line.
You also need to consider insurance and budget for cybercrime. The government’s cyber essentials scheme is very limited, so I’d recommend looking for additional coverage options. I have recently bought into a new product here at Westway IT that includes cyber essentials certification and offers an upgrade on the insurance, but I ask that clients consider where they need additional, more bespoke plans. Setting aside a budget for cybercrime isn’t a bad plan either; it allows you to act quickly in the event of an attack. Think of it as a contingency.
I advocate a proactive approach to safeguarding your business. One of the most effective strategies is considering your cybersecurity defences as a series of layers, each contributing to a robust shield against potential threats.
Layered security involves deploying multiple security measures across various points within your IT infrastructure. Each layer serves as a defence mechanism that adds complexity for cybercriminals and makes it more challenging for them to breach your systems. The beauty of this approach is versatility; it can be customised to fit your business's unique needs and budget.
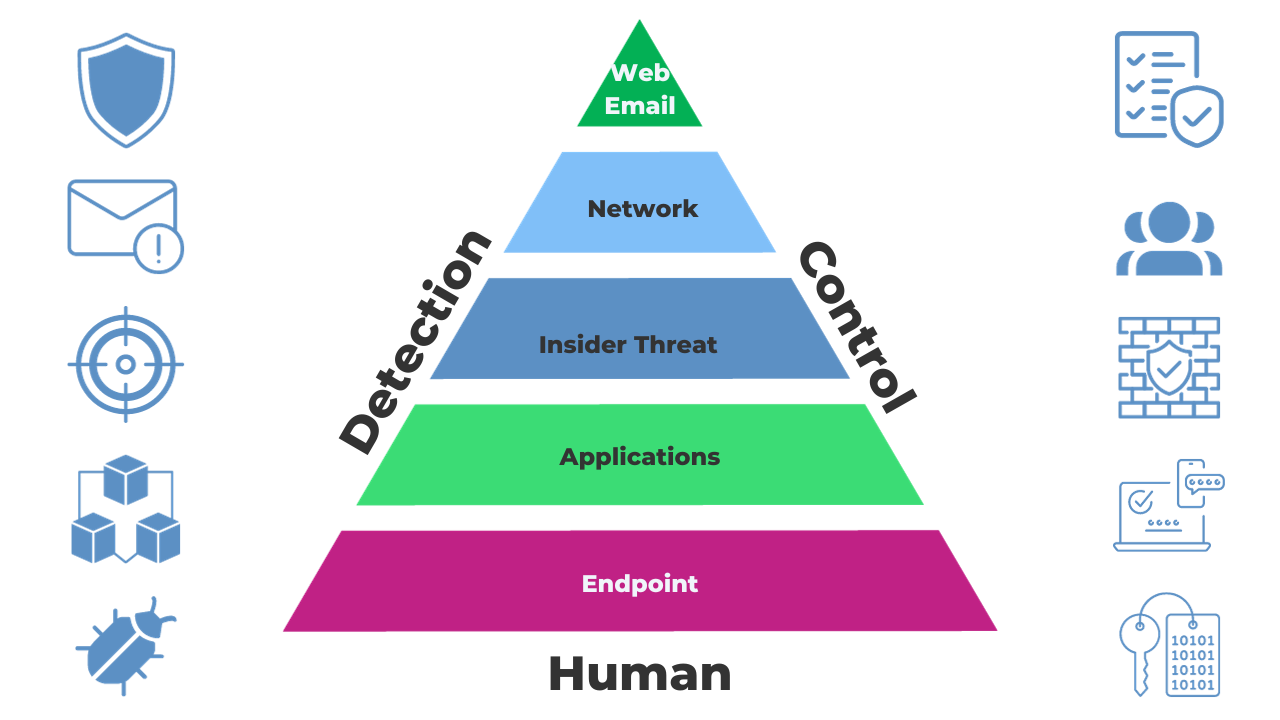
One integral component of layered cybersecurity is the concept of zero-trust. In today's interconnected digital world, trust can no longer be assumed based on location or network perimeter. A zero-trust cybersecurity policy means trust is never assumed, even within your organisation's boundaries. This approach ensures that every user, device, or application is verified and authorised before accessing sensitive resources.
Implementing a zero-trust framework involves granular access control, continuous monitoring, and real-time threat detection. It means verifying every user and device's identity and security posture, whether inside or outside your network. This approach significantly reduces the risk of unauthorised access and lateral movement by threat actors within your systems.
Understanding that cybersecurity is not a one-time investment or a set-it-and-forget-it endeavour is crucial. Instead, it's an ongoing process that requires constant vigilance and adaptation. The cyber threat landscape is ever-evolving, and cybercriminals continually develop new tactics. By embracing the principles of layered security and zero trust, you establish a solid foundation to adapt and respond to emerging threats effectively.
Okay, so how do you get started? Well, you start by looking at your security hygiene.
Think of your business's security hygiene as the daily routine that keeps your digital environment healthy and secure. It's crucial that you are consistent in maintaining it and adapting it as your needs change. It's also where you'll spot potential problems.
One of the fundamental pillars of cybersecurity hygiene is ensuring that all your software, operating systems, and applications are up to date. Cybercriminals often exploit vulnerabilities in outdated software.
Your employees are always your first line of defence against cyber threats. However, they can also inadvertently become entry points for attackers if not adequately trained and aware. That's why employee training is a critical aspect of cybersecurity hygiene. It involves educating your staff about phishing emails, social engineering tactics, and safe online behaviour. When your employees are vigilant and knowledgeable about cybersecurity risks, they become invaluable assets in your security strategy.
Beyond training, fostering a cybersecurity-conscious culture within your organisation is paramount. This culture shift involves instilling a sense of responsibility among your team members. They should understand that cybersecurity is not solely the IT department's concern but a collective effort to protect the business.
Encourage open communication about security incidents or potential threats. Make reporting easy and non-punitive so that employees feel comfortable raising concerns. Emphasise the importance of strong, unique passwords and multi-factor authentication. These small steps can collectively create a robust cybersecurity culture.
In addition to proactive measures, periodic cybersecurity audits and assessments are essential to maintaining a solid security posture. These assessments help identify vulnerabilities, evaluate the effectiveness of existing security controls, and provide insights into areas that need improvement.
Investing in the right cybersecurity tools is another aspect of maintaining cybersecurity hygiene. These tools can include firewalls, antivirus software, intrusion detection systems, and encryption solutions. The choice of tools should align with your specific security needs and risk profile.
Now that we've been proactive, let's look at mitigation and response because, in the future, you'll be grateful you continued reading.
Despite your best efforts in implementing layered security, zero trust policies, and maintaining cybersecurity hygiene, it's essential to acknowledge that no organisation is entirely immune to cyber threats. Breaches can and do occur. How you react and, most importantly, how you take proactive steps today will help you limit the fall-out.
When a system breach occurs, time is of the essence. A swift and informed response can make a significant difference in minimising damage. Your response begins with identifying the breach, understanding its scope, and assessing the potential impact on your business. That phase will often involve your IT team or cybersecurity consultant to gather crucial information.
Make sure you also contact your cyber insurance provider. That will help start claim paperwork for costs incurred during your response process.
You will also need to know what level of data penetration you are dealing with. If breached data includes sensitive information, you must contact the ICO. Here’s a link to their breach report page.
Having a well-defined incident response plan is paramount, especially when you are under pressure. Your plan serves as your roadmap to navigate the chaos of a cybersecurity incident. It outlines roles and responsibilities, communication protocols, and specific actions to take during a breach. Your incident response plan should cover containment, eradication, recovery, and lessons learned.
Where you have cyber insurance, you must create tasks for those responsible for keeping your policy provider updated. You may invalidate your incident claim if you don’t alert your policy provider early enough. My best advice is to ensure you understand your policy in every detail to plan ahead without any nasty surprises.
Containment is the initial phase of response. It involves isolating the affected systems and limiting the breach's ability to spread further within your network. Quick and decisive action in this phase can prevent the situation from escalating.
Once containment is achieved, the next step is eradication. That involves identifying and removing the root cause of the breach. It may require system patching, malware removal, or other technical interventions. In this phase, your IT team or cybersecurity consultant will attempt to eliminate and prevent the threat from recurring.
After containment and eradication, your focus shifts to recovery. This phase includes restoring affected systems to their normal functioning state. Depending on the breach's severity, this can be complex and time-consuming. Ensuring you have a business continuity plan in place will be important here. During recovery, it's essential to ensure that all systems are secure before returning them online.
Backups are your root to getting back up and running quickly. Remember, a plugged-in hard drive is not good enough - it can be outdated or affected by attacks. Make sure you invest in a fully restorable backup system. You really don’t want to tell your clients you lost three weeks of data!
The final aspect of incident response is conducting a post-incident analysis, a critical step in continuous improvement. It involves a comprehensive incident review, identifying vulnerabilities, and evaluating your response. The lessons learned from each incident should inform your business continuity plan, cybersecurity strategy and incident response plan updates.
Encryption and data protection play a pivotal role throughout the incident response process. These measures ensure that sensitive data remains secure, even during a breach. Encryption keeps your data unintelligible to unauthorised users, limiting the damage a breach can cause.
If you haven’t set this up, it’s time to implement it!
In light that I may have broken your ideal that perfection in cybersecurity is possible, I hope I have shown you that prioritising preparedness and response can bolster your business's resilience against cyberattacks.
Please assess your cybersecurity measures regularly and consider professional guidance, regardless of your business's size. Cybersecurity is a shared responsibility; together, we can fortify your digital defences.
Are you looking for a personalised cybersecurity consultation tailored to your business?
Hi, I'm John Fisher, and I offer IT support, business services, and hardware to micro and small businesses in and around Gloucestershire. My mission is to help small companies to be more efficient by providing innovative IT solutions that meet their unique needs - including business and cyber resilience.
Join me for a free 15-minute consultation, and let's talk through your cyber security update.

John Fisher
Meet John Fisher, founder of Westway IT, passionate about helping businesses thrive with technology. With a BSc in Computer Science, he values integrity, education, and quality relationships. Active in The Tech Tribe and GTIA, John simplifies IT and creates scalable strategies. Connect with him on LinkedIn.