How a TBR Can Save You Time and Boost Efficiency
Discover how a TBR can streamline your business with automation, AI, and e-signatures
VideoAre you having trouble with clients and suppliers receiving your emails, or maybe you are wondering why emails from clients and suppliers are going to spam?
The answer is simple and twofold, it’s either because your DNS data is ill-configured, or more than likely you are making common mistakes that are causing your emails to get flagged as spam.
In this blog post, we want to show you what’s happening in email security and why the game is changing and what you can do to create better emails that land correctly.

Cybercrime has exploded since the pandemic, according to Interpol and criminals are using the fear and uncertainty of Covid, the recession and political unrest to exploit their victims. If we think about it it’s easy to see where business owners and employees are falling into the traps that hackers are leaving them if their minds are elsewhere.
From April 2021 to March 2022 the office of National Statistics reported 4.5 million fraud attacks, a rise of 25% from pre-pandemic times. Two-thirds of these attacks were online phishing scams committed by email, social media or text messages. Most hits were users between the ages of 25 and 44, who lost personal identifiers that led to bank or credit account fraud and customer or retail fraud.
As a result of increased threats, email providers like Microsoft are taking the lead to improve their email security.
In Microsoft’s own research around the pandemic, they found that 62% of security professionals including SOC Analysts, security admins and CISOs reported more phishing email campaigns during this period. IT professionals went on to say that they believed security issues increased as concerns appeared to be related to downloading content and accessing work information on remote, private WiFi networks that may not be as secure as work connections.
Whilst some of these situations may be avoided now that IT professionals and staff are back in the office, post-pandemic, Microsoft recognised that the cost to business each year (reported by IBM as $4.65 million, or £3.75 million in 2022) was rising and so made steps to improve their email defence systems.
At the same time, email hosts also recognise that businesses are operating differently than they were pre-pandemic. Most businesses now offer a wider range of device options for employees to use in hybrid working environments. This means that changes are not just about filtering our cybercrime, but also about device protection.
This is where AI comes in. If we look at Microsoft’s email security protection software, Exchange Online Protection, which comes as standard, we can see they have improved it to include updates on known threats. For 365 premium users, there is the new Safe Links, which filters highly suspicious emails to a sandbox for security administrators to manually filter. This human-operated approach to enhancing security creates a safer environment for businesses still.
But that doesn’t stop spam from getting in and it also increases the risk of poorly set up emails going to spam folders.
As we mentioned earlier there are two reasons why your emails are not delivering as they should; firstly your DNS data is ill-configured, or secondly, you are making common formatting mistakes.
Before we fix that, let’s look at how email authentication works.
When you send an email, the server you send it from signifies the legitimacy of your email to the recipient’s email server (which can be configured in your DNS settings). Security software filters out anything that doesn’t have a validated or approved server as the host of that sent email.
There are two common types of email authentication
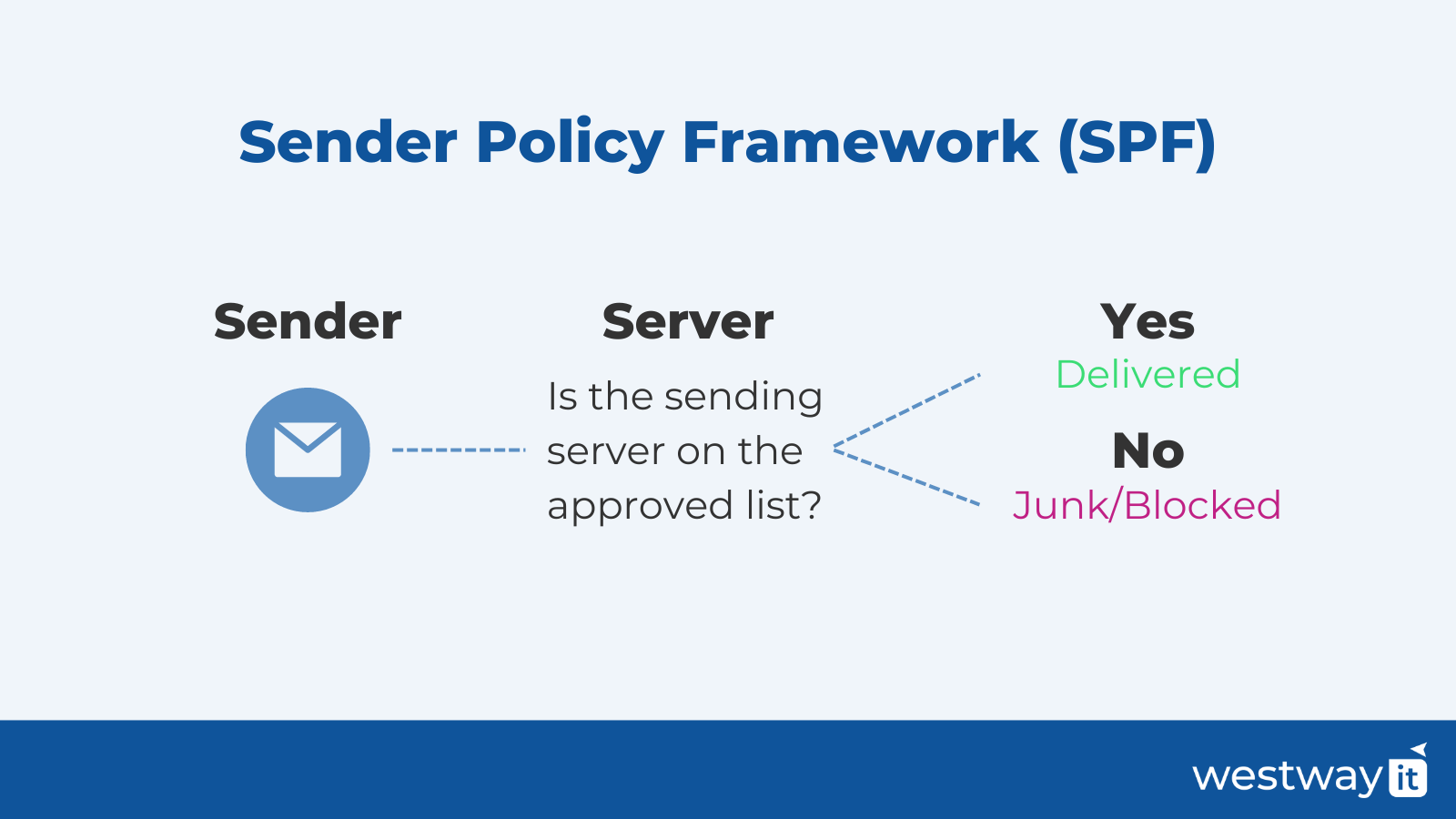
Sender Policy Framework (SPF) was developed in the early 2000s and as a method of authentication uses DNS records to identify verified sources. It looks something like this.
Domain Keys Identified Email (DKIM) authentication is a method that includes a private digital key signature along with DNS record verification to match a public key record - an extra layer of security.
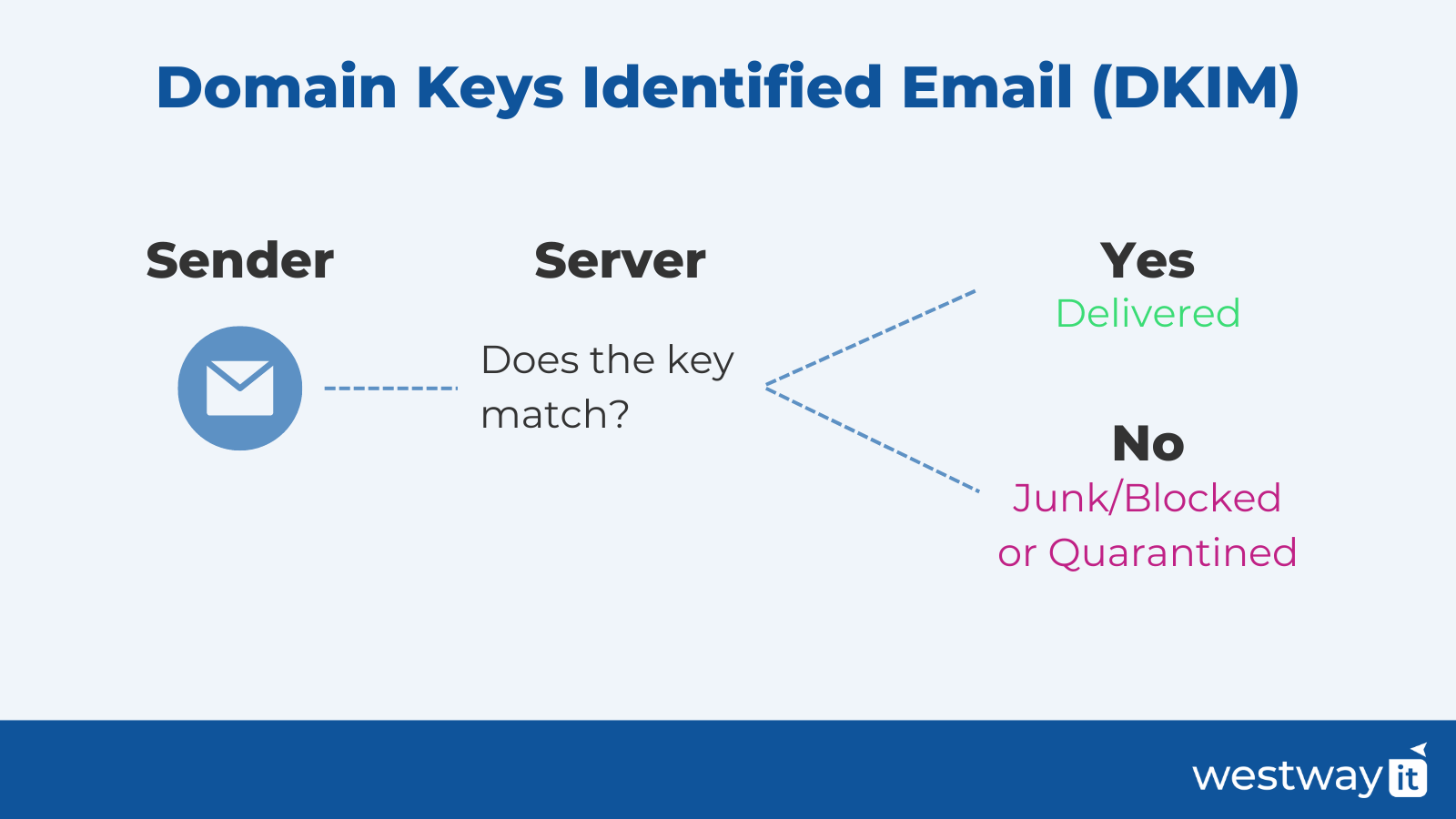
It’s a bit like saying to your sender, “Here’s my email and here’s my digital signature to say that my email is verified, unaltered and sent securely from my domain.”
To configure your DNS records you need to authenticate your domain. Depending on your provider the process will look different, but essentially you are looking to
You will need to contact your email provider or IT professional if you are finding it hard to locate your DNS records for SPF and DKIM keys.
Email security isn’t just looking for authentication passes anymore, instead, it is looking for indicators within an email. Let’s run through some formatting issues that might be causing you problems.
As Microsoft partners, Westway IT is in a unique position to be able to help you implement M365 and other Microsoft software across your business and its devices. We are specialists in handling sensitive data, as many of our clients’ industries have regulatory requirements.
We have seen many of our clients through the Pandemic and everything the dark web has had to throw at them, so we understand the importance of multiple-device handling and hybrid-working protocols.
Your business emails are crucial. They aren’t just tools for communication, they are instruments that help you deliver work, secure payments and manage client relationships. It means that having each of your emails arrive exactly when you want them to, and to whom you want them to arrive is vital.
If you need help with email deliverability book a 15-minute consultation.

John Fisher
Meet John Fisher, founder of Westway IT, passionate about helping businesses thrive with technology. With a BSc in Computer Science, he values integrity, education, and quality relationships. Active in The Tech Tribe and CompTIA, John simplifies IT and creates scalable strategies. Connect with him on LinkedIn.